Risk-rules-of-public-blockchain
Learn about money laundering in one movie
一口气了解洗钱 它能玩得有多花 — 小Lin说
https://www.youtube.com/watch?v=s3iM7VslPsQ
Behavior 行为模式
peeling chain 剥皮链
A peeling chain is a behavioral pattern where multiple repeated deposits are made at an exchange or service. A peeling chain pattern may suggest an attempt to stay below a certain KYC threshold to avoid detection.
剥皮链是指在交易所或服务平台上反复进行多次存款操作。剥皮链模式可能意味着试图保持在某个KYC阈值以下,以避免被检测到。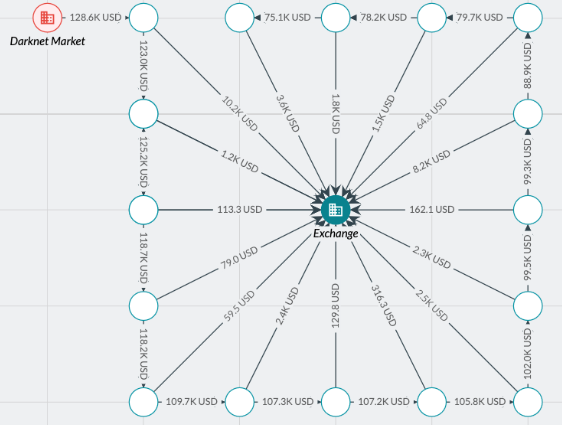
举例 - 在2022年初,一些犯罪分子利用剥皮链技术在多家加密货币交易所进行小额频繁的存款操作,以保持在KYC合规的最低要求之下,从而避免被交易所标记为高风险账户。这些小额存款随后被转移到多个中间账户,最终汇集到一个主要的钱包地址,用于购买非法商品或进行洗钱活动。
reference link ==> https://www.fraudinvestigation.net/cryptocurrency/tracing/peel-chain
automated layering 自动分层
Automated layering, also called artificial hops, is a behavioral pattern that involves routing funds through multiple intermediate hops without any dilution of funds. An automated layering pattern may suggest an attempt to obfuscate the true source of funds by exploiting the fact that some screening programs will stop tracing at a certain number of hops.
自动分层,也称为人工跳跃,通过多次中间跳跃路由资金,而不稀释资金总额。自动分层模式可能表明企图利用某些筛查程序在一定跳跃次数后停止追踪的特点,来掩盖资金的真实来源。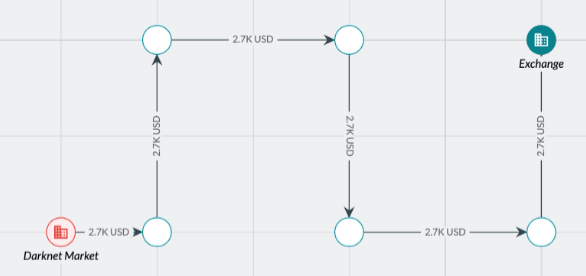
实例 - 2023年,某犯罪团伙利用自动分层技术,将通过诈骗和勒索所得的加密货币资金,在短时间内通过多个区块链地址进行中转,每次转移均未稀释资金总量。整个操作过程中,资金经过超过20次跳跃,旨在逃避追踪和监管机构的监控。这种行为利用了部分筛查程序的限制(即超过一定次数的跳跃后停止追踪)。
reference link ==> https://www.fraudinvestigation.net/cryptocurrency/tracing/layering
mixer first funding 首次混币资助
Mixer first funding is a tactic used during high-profile exploits. Bad actors fund their attack addresses using a Mixer or Coin Swap Service to hide the original source of funds. While these services aren’t illegal in themselves, they allow users to obscure fund origins, which can facilitate illicit activities. This behaviour flags when addresses receive their first transaction from a mixer or low-KYC exchange.like Tornado Cash.
首次混币资助是在高调攻击事件中使用的策略。恶意行为者通过混币器或币交换服务为其攻击地址提供资金,以隐藏资金的原始来源。尽管这些服务本身不违法,但它们允许用户掩盖资金来源,可能助长非法活动。当地址接收到来自混币器或低KYC交易所的首次交易时,这种行为会被标记。例如,Tornado Cash。
在韩国,一起针对某知名区块链项目的攻击中,黑客利用混币器为攻击钱包地址提供初始资金。黑客通过混币服务掩盖了资金来源,然后对该区块链项目的智能合约漏洞进行了攻击,盗取了价值数千万美元的加密货币。
address poisoner 地址投毒者
Address Poisoner identifies addresses that conducted an address poisoning attack. Address poisoning, also known as address spoofing, is a scam where fraudsters create a fake wallet address resembling the user’s or one frequently used by them. Using this fake address, they send small amounts of cryptocurrency or NFTs to the user’s wallet, which ‘poisons’ the transaction history with deceitful transactions. They anticipate that the user, failing to notice the difference due to the address similarity, will unwittingly use the scam address for transactions - resulting in the loss of funds.
地址投毒者识别那些进行了地址投毒攻击的地址。地址投毒(也称地址欺骗)是一种骗局,骗子创建一个伪造的、与用户常用地址相似的钱包地址,并向用户的钱包发送少量加密货币或NFT,从而“污染”交易历史,使其充满欺骗性的交易记录。他们预期用户因地址相似而未能发现差异,从而在进行交易时不经意地使用了骗局地址,导致资金损失。
2022年底,美国一名诈骗者在某用户频繁使用的加密货币地址基础上,创建了一个仅在最后几位字符上不同的假冒地址。诈骗者利用这一相似地址,向受害者的钱包发送少量加密货币,希望受害者在未来的交易中误用该假冒地址,导致资金转入诈骗者控制的钱包。受害者没有仔细核对地址,误将价值数千美元的加密货币转入诈骗者的钱包。尽管事后发现了问题,但资金已无法追回。
1)诈骗者可以通过编写脚本,自动生成大量的地址,然后筛选出与目标地址相似的地址。由于每次生成的地址都是不同的,只要生成足够多的地址,总能找到一个与目标地址在某些位置上相似的地址。这个方法类似于“暴力破解”,需要大量的计算资源,但可以通过批量生成和筛选来实现。2)有些加密货币钱包允许用户使用一些工具(如Vanitygen)来生成“个性化”的地址,即地址的部分字符是可以指定的。这些工具允许用户设定地址的前缀或后缀,然后通过不断尝试生成满足条件的地址。例如,可以通过不断生成和筛选找到一个以特定字符或数字结尾的地址,从而与目标地址形成相似性。
exploiter 攻击者
Leverage this rule to mitigate interaction with addresses that have participated in a hack or exploit.
通过此规则,可以减少与曾参与黑客攻击或漏洞利用的地址之间的互动。
Ice phishing 冰钓式网络钓鱼
Ice phishing occurs when a user unknowingly allows a scammer to control their wallet. The scammer tricks the user into approving a transaction that looks safe, but in reality, the approval is granted to the scammer’s address hidden in transaction data. Once the approval is given, the attacker can take control over their digital assets. Leverage this rule to prevent interactions with addresses that have performed ice phishing attacks.
冰钓式网络钓鱼发生在用户在不知情的情况下允许诈骗者控制他们的钱包时。诈骗者诱骗用户批准一项看似安全的交易,但实际上,交易数据中隐藏的批准地址是诈骗者的。一旦批准,攻击者就可以控制用户的数字资产。通过此规则可以防止与执行冰钓式网络钓鱼攻击的地址进行交互。
2023年3月,英国某用户在一次空投活动中,批准了一项授权交易,实际上授权的是一个隐藏在交易数据中的恶意地址。该恶意地址由诈骗者控制,一旦获得授权,诈骗者迅速将用户的钱包中的代币转移至自己的钱包。受害者损失了价值超过50万美元的加密货币,而诈骗者利用多个分层账户迅速洗白这笔资金,避免了被追踪。
原理说明
- 诱饵设定:诈骗者通常会通过某种诱饵,比如伪造的空投、假冒的DApp(去中心化应用)或钓鱼网站,诱导用户进行某项操作。
- 授权请求:当用户点击“领取空投”或进行其他操作时,网站或应用会弹出一个交易请求,让用户授权某个智能合约或地址管理其代币。用户通常会认为这是一个安全的操作,实际上授权的地址是攻击者的恶意地址。
- 恶意授权:用户一旦确认交易,攻击者就获得了代币的控制权限,可以任意转移受害者的资产。
代码实例
以下是一个示例,以ERC20代币为例,展示如何构造一个授权交易,并潜在地进行恶意操作:
1 | // 使用以太坊Web3库构造授权交易 |
攻击过程
一旦授权完成,恶意地址将获得代币转移的权限。诈骗者可以使用transferFrom方法,将受害者的代币转移到自己控制的钱包。
1 | // 转移代币的代码示例(攻击者执行) |
防范措施
• 仔细检查授权地址:用户在确认授权交易时,应该仔细检查授权的地址,确保不是恶意地址。
associated scammer address 关联诈骗者地址
Leverage this rule to mitigate interaction with addresses that have received funds from a known scammer.
通过此规则,可以减少与曾接收过已知诈骗者资金的地址之间的互动。
scammer deployed contract 诈骗者部署的合约
Leverage this rule to mitigate interaction with smart contracts deployed by known scammers. These contracts often promise high returns or false investments but are designed to siphon funds once the victim interacts with them. You can expand this section by discussing how smart contracts are audited (or not) and why code auditing practices could help detect scammer-deployed contracts early.
通过此规则,可以减少与已知诈骗者部署的智能合约之间的互动。这些合约通常承诺高回报或虚假投资,但其目的是在受害者与其互动后吸走资金。讨论如何审计智能合约(或不审计)以及为什么代码审计实践可以帮助及早发现诈骗者部署的合约来扩展此部分。
pig butchering 杀猪盘
Pig Butchering is a scam that utilizes deceptive communications to manipulate individuals into making fraudulent investments. This behavior identifies addresses that have received transactions suspected to be from Pig Butchering victims. This is accomplished by analyzing historical transactions made by victims of Pig Butchering.
杀猪盘是一种利用欺骗性沟通来操控个人进行虚假投资的骗局。该行为识别接收到疑似来自杀猪盘受害者交易的地址。这是通过分析杀猪盘受害者的历史交易实现的。
2023年7月,东南亚一个国际诈骗团伙通过社交平台接触受害者,利用情感交流和投资诱惑逐渐获取受害者的信任,随后引导受害者向所谓的“高收益投资项目”转账,实际上这些资金都进入了诈骗者控制的钱包。多个受害者损失金额高达数百万美元。受害者在察觉被骗后报案,但由于资金早已被分散转移至多个国家的加密货币账户,追查和追回难度极大。
Exposure
Detect exposure to labeled entities using various risk triggers 意思是识别与某些特定类别的实体(如企业、个人或组织)之间的潜在风险关联。
系统通过多种风险触发器来检测用户或地址与这些标记的实体之间的交互情况。这些实体通常被标记为与特定的高风险活动相关:
1. Activist Fundraising (政治/社会运动筹款)
与政治或社会运动相关的筹款活动,可能涉及高风险或敏感的资金来源,存在被利用进行非法活动的风险。
Associated with political or social movement fundraising, potentially involving high-risk or sensitive fund sources, and could be used for illegal activities.
2. ATM (加密货币自动取款机)
加密货币ATM允许用户将加密货币兑换成现金或反向操作,因其匿名性和现金交易特性,可能被用于洗钱活动。
Cryptocurrency ATMs allow users to convert crypto into cash or vice versa. Due to their anonymity and cash-based transactions, they can be used for money laundering.
3. Authentication (身份认证服务)
涉及身份认证服务,可能存在身份欺诈和非法账户访问的风险。
Involves identity authentication services, which could carry risks related to identity fraud and unauthorized account access.
4. Bitcoin Faucet (比特币水龙头)
提供少量免费比特币的网站,可能被用于隐匿资金来源或洗钱。
Websites that distribute small amounts of free Bitcoin, potentially used to obscure the source of funds or launder money.
5. Bridge (跨链桥服务)
跨链桥服务用于在不同区块链之间转移资产,可能增加资金追踪的难度。
Cross-chain bridges allow asset transfers between different blockchains, which can complicate fund tracing.
6. Broker (经纪商/中介服务)
未经许可的金融中介服务,可能涉及非法金融活动或欺诈。
Unlicensed financial intermediaries, potentially involved in illegal financial operations or fraud.
7. Charity (慈善机构)
某些慈善机构可能被用于洗钱或掩盖非法资金流动。
Some charity organizations may be used for money laundering or concealing illegal fund flows.
8. Child Sexual Abuse Material Vendor (儿童性虐待材料供应商)
涉及儿童性虐待材料的交易,是严重的非法活动风险指示。
Involves the trade of child sexual abuse material (CSAM), a severe indicator of illegal activity.
9. Coin Swap Service (币种兑换服务)
币种兑换服务用于将一种加密货币兑换为另一种,可能被用于洗钱或隐藏资金来源。
Coin swap services exchange one cryptocurrency for another and may be used for money laundering or hiding the source of funds.
10. Credit Card Data Vendor (信用卡数据供应商)
非法出售信用卡数据的服务,常用于网络犯罪和欺诈。
Services that illegally sell credit card data, often used in cybercrime and fraud.
11. Criminal Organization (犯罪组织)
与已知犯罪组织相关的实体,这些组织涉及洗钱、勒索等非法活动。
Entities associated with known criminal organizations involved in activities such as money laundering, extortion, etc.
12. Dark Forum (暗网论坛)
暗网上的非法讨论平台,常用于信息交易和非法商品交易。
Illicit discussion platforms on the darknet, often used for information exchange and the trade of illegal goods.
13. Dark Market – Centralized (中心化暗网市场)
提供非法商品和服务的中心化暗网市场。
Centralized darknet markets offering illegal goods and services.
14. Dark Market – Decentralized (去中心化暗网市场)
去中心化的非法商品和服务交易市场,难以追踪和关闭。
Decentralized marketplaces for trading illegal goods and services, harder to trace and shut down.
15. Dark Service (暗网服务)
提供匿名代理、伪造文档等非法服务的平台。
Platforms providing illegal services such as anonymous proxy, forged documents, etc.
16. Dark Vendor Shop (暗网供应商店)
在暗网市场上设立的供应商店,提供非法商品或服务。
Vendor shops on darknet markets providing illegal goods or services.
17. Extortion (勒索)
通过威胁或强制手段获取资金,常见于勒索软件攻击中。
Obtaining funds through threats or coercion, commonly seen in ransomware attacks.
18. FinCEN Primary Money Laundering Concern (FinCEN主要洗钱关注对象)
被美国金融犯罪执法网络(FinCEN)认定为主要洗钱对象。
Entities identified by the U.S. FinCEN as primary money laundering concerns.
19. Gambling (赌博)
在线赌博服务,可能与资金洗白、欺诈有关。
Online gambling services, potentially associated with money laundering or fraud.
20. Known Criminal (已知犯罪分子)
已被确认与犯罪行为有关联的实体,涉及欺诈、盗窃等活动。
Entities known to be involved in criminal activities such as fraud, theft, etc.
21. Malware (恶意软件)
涉及恶意软件的交易,这些软件用于窃取资金或敏感信息。
Transactions involving malware used to steal funds or sensitive information.
22. Marijuana Vendor Shop (大麻销售店铺)
销售大麻的商店,在一些地区可能非法。
Shops selling marijuana, which may be illegal in certain jurisdictions.
23. Mixer (混币服务)
混币服务用于混淆加密货币的资金来源,常用于洗钱。
Mixing services used to obscure the source of cryptocurrency, often for money laundering.
What Kind of Service is CoinJoin?
CoinJoin is a privacy-enhancing Bitcoin transaction which combines inputs from numerous users and returns multiple outputs of identical values. Unlike other mixing services, users maintain custody of their funds throughout this process.
The uniformity of outputs is intended to obscure ownership of each UTXO and defeat the heuristic-based clustering algorithms used by law enforcement and blockchain investigators.
For example, if four users input 2, 4, 6 and 8 BTC for a total of 20 BTC, the CoinJoin transaction would create 20 separate outputs each worth 1 BTC. The outputs would be apportioned to each user in the same amounts they originally contributed. Since every output has the same value, it should be impossible (in theory) to immediately discern which of the new bitcoin addresses are now controlled by each of the original four users.
24. OFAC Sanctioned Entity (OFAC制裁实体)
受到美国外国资产控制办公室(OFAC)制裁的实体。
Entities sanctioned by the U.S. Office of Foreign Assets Control (OFAC).
25. Phishing (网络钓鱼)
通过欺诈手段获取用户敏感信息(如私钥或登录凭证),常见于网络钓鱼攻击。
Fraudulently obtaining sensitive user information (e.g., private keys or login credentials), common in phishing attacks.
26. Ponzi Scheme (庞氏骗局)
一种非法的投资骗局,承诺高额回报,但实际上利用新投资者的资金支付旧投资者的收益。
An illegal investment scam promising high returns, but actually uses new investors’ funds to pay previous investors.
27. Privacy Wallet (隐私钱包)
注重隐私保护的钱包,可能被用于隐藏交易历史或资金流动。e.g., Wasabi Wallet。
Privacy-focused wallets designed to conceal transaction histories or fund flows. e.g., Wasabi Wallet.
28. Ransomware (勒索软件)
勒索软件攻击中使用的地址,受害者需支付赎金解锁被恶意加密的数据。
Addresses involved in ransomware attacks, where victims pay ransoms to unlock maliciously encrypted data.
29. Scam (诈骗)
涉及诈骗活动的实体或地址,这些地址可能用于网络钓鱼或其他形式的欺诈。
Entities or addresses involved in fraudulent activities, often used in phishing or other types of fraud.
30. Shielded (隐私交易)
通过隐私保护技术(如零知识证明)隐藏交易信息的工具。
Tools that use privacy-enhancing techniques (like zero-knowledge proofs) to hide transaction details.
31. Thief (盗窃)
涉及盗窃加密货币的地址,通常通过未经授权的访问或攻击行为。
Addresses involved in cryptocurrency theft, typically via unauthorized access or hacking.
32. Terrorist Organization (恐怖组织)
涉及恐怖组织的资金流动。
Transactions associated with terrorist organizations.
33. Human Trafficking (人口贩运)
与人口贩运相关的资金流动。
Transactions related to human trafficking activities.
34. Weapon Sales (武器销售)
非法武器销售相关的资金流动。
Transactions involving the illegal sale of weapons.
35. Drug Trafficking (毒品贩运)
与非法毒品交易相关的资金流动。
Transactions related to the illegal drug trade.
36. Sanctioned Countries (受制裁国家)
与受国际制裁国家的交易,可能违反国际法。
Transactions with entities from sanctioned countries, potentially violating international law.
37. Shell Companies (空壳公司)
被用于洗钱或隐藏非法资金来源的空壳公司。
Shell companies used for money laundering or hiding illegal fund sources.
38. High-Risk Jurisdictions (高风险司法管辖区)
与高腐败或监管薄弱的国家或地区的交易,可能增加洗钱风险。
Transactions with countries or regions known for weak regulations or high corruption, increasing money laundering risks.
39. Fraudulent ICO (欺诈性ICO)
假冒的初始代币发行,承诺高额回报但无实际项目支持。
Fake Initial Coin Offerings (ICOs) that promise high returns but have no real project backing.
40. Illegal Content (非法内容)
传播或交易非法内容(如盗版、暴力、仇恨言论),这些行为通常违反法律。
The distribution or trade of illegal content (e.g., pirated material, violence, hate speech), which typically violates the law.
41. Illicit Marketplace (非法市场)
从事非法商品或服务交易的市场,这些市场往往涉及洗钱、毒品或武器交易。
Marketplaces that deal in illegal goods or services, often involving money laundering, drug trade, or weapons transactions.
42. Money Mule (资金骡子)
通过第三方账户转移非法资金的活动,这些账户通常不知情或自愿参与。
Involves the transfer of illicit funds through third-party accounts, where the account holders may be unaware or willingly participate.
43. Ponzi-like Scheme (类庞氏骗局)
与庞氏骗局类似的投资骗局,承诺高额回报但实际上以新的投资者资金支付旧投资者的收益。
A fraudulent investment operation similar to a Ponzi scheme, promising high returns while using new investors’ money to pay earlier investors.
44. Privacy Coin (隐私币)
设计用于隐藏交易细节的加密货币,虽然保护用户隐私,但也可能被用于非法活动。
Cryptocurrencies designed to conceal transaction details, while enhancing user privacy, may also be used for illicit activities.
45. Ransomware Payment (勒索软件支付)
向勒索软件攻击者支付赎金的交易,用以解锁被恶意加密的数据。
Transactions made to ransomware attackers to unlock maliciously encrypted data.
46. Sanctioned Individual (受制裁个人)
与受国际或政府制裁的个人进行交易,可能违反制裁法律。
Transactions with individuals under international or government sanctions, potentially violating sanction laws.
47. Suspicious Transaction (可疑交易)
异常或可疑的交易行为,可能与洗钱、欺诈或其他非法活动相关。
Transactions that appear abnormal or suspicious, potentially linked to money laundering, fraud, or other illicit activities.
48. Terrorist Financing (恐怖主义融资)
为恐怖组织提供资金的行为,通常通过加密货币隐秘进行。
The act of providing financial support to terrorist organizations, often facilitated covertly through cryptocurrency.
49. Unlicensed Money Service Business (无牌照货币服务业务)
未经许可的货币兑换或转账服务,可能涉及洗钱或非法金融活动。
Unlicensed currency exchange or transfer services, potentially involved in money laundering or illegal financial activities.
50. Whale Transaction (巨鲸交易)
涉及大量加密货币交易,可能引起市场波动或被用于非法资金转移。
Transactions involving large amounts of cryptocurrency, potentially affecting market stability or used for illicit fund transfers.
51. Front-Running (抢跑交易)
涉及利用未公开的市场信息,在合法交易被确认之前抢先执行交易,导致市场操纵或不公平的交易环境。
Front-running involves using non-public market information to execute trades before legitimate trades are confirmed, leading to market manipulation or unfair practices.
52. Pump-and-Dump (拉高出货)
一种市场操纵手段,操纵者人为抬高加密货币的价格,吸引散户投资者购买,随后抛售手中的大量持仓。
A form of market manipulation where perpetrators artificially inflate the price of a cryptocurrency to attract retail investors, then sell off their large holdings.
53. Wash Trading (刷单交易)
交易者通过自己在不同账户间反复买卖相同资产,制造虚假交易量,操纵市场价格。
Traders repeatedly buy and sell the same asset between their own accounts, creating fake trading volume to manipulate market prices.
54. Regulatory Arbitrage (监管套利)
利用不同司法管辖区的监管差异,通过选择监管较宽松的地区进行交易,规避合规要求。
Taking advantage of regulatory differences across jurisdictions by trading in regions with looser regulations to avoid compliance requirements.
=============== the risks below are not in the list of Elliptic and TRMLAB ===============
================= 以下风险没有包含在 Elliptic and TRMLAB 的范围内 =================
55. Fake News Manipulation (假新闻操纵)
散布虚假消息,影响市场情绪和资产价格,从中获利或导致市场动荡。
Spreading false information to manipulate market sentiment and asset prices, either for profit or to destabilize the market.
56. Tax Evasion (逃税)
使用加密资产来隐瞒收入,逃避税收,特别是在多个国家拥有资产的情况下。
Using cryptocurrencies to hide income and evade taxes, especially when assets are held across multiple countries.
57. Insider Trading (内幕交易)
未公开的内部信息被用于个人利益相关的交易,可能违反证券法。
Using non-public insider information for personal gain in trading, potentially violating securities laws.
58. Peer-to-Peer (P2P) Market Risks (点对点市场风险)
在P2P交易市场上,用户可以绕过银行或正规金融机构进行交易,增加欺诈或非法交易的风险。
On peer-to-peer markets, users can bypass banks or formal financial institutions, increasing the risk of fraud or illicit transactions.
59. Layer 2 Protocol Risks (Layer 2协议风险)
涉及Layer 2扩展方案的风险,这些方案用于提高区块链交易的可扩展性,但可能缺乏充分的安全性或合规措施。
Risks related to Layer 2 scaling solutions, which aim to improve blockchain transaction scalability but may lack robust security or compliance measures.
60. Flash Loan Exploits (闪电贷攻击)
使用无抵押的闪电贷款,在单个交易中操纵市场或智能合约,进行非法获利。
Using uncollateralized flash loans to manipulate the market or smart contracts within a single transaction for illicit profit.
61. Smart Contract Exploits (智能合约漏洞利用)
利用智能合约中的漏洞或缺陷,执行未授权的资金转移或操纵合约行为。
Exploiting vulnerabilities or flaws in smart contracts to carry out unauthorized fund transfers or manipulate contract behavior.
62. NFT Fraud (NFT欺诈)
与非同质化代币(NFT)相关的欺诈行为,包括伪造稀有资产、洗钱或欺骗性交易。
Fraud involving Non-Fungible Tokens (NFTs), including forgery of rare assets, money laundering, or deceptive transactions.
63. Liquidity Pool Exploitation (流动性池利用)
通过操纵流动性池的算法或规则非法获利,导致投资者或交易者损失。
Illegally profiting by manipulating the algorithms or rules governing liquidity pools, causing losses to investors or traders.
64. DeFi Protocol Risks (去中心化金融协议风险)
去中心化金融(DeFi)平台的风险,包括智能合约漏洞、治理攻击、流动性枯竭等。
Risks associated with decentralized finance (DeFi) platforms, including smart contract vulnerabilities, governance attacks, and liquidity exhaustion.
65. Unregulated Stablecoins (无监管稳定币)
某些稳定币未受监管,可能在破产、赎回失败或资产透明性不足的情况下带来系统性风险。
Some stablecoins are unregulated, potentially posing systemic risks in the event of insolvency, redemption failures, or lack of transparency.
What Kind of Information Can be Traced?
The twin goals of cryptocurrency forensics and asset tracing — identify the perpetrator, and find their funds — are pursued through several areas of analysis and fact-finding:
Attribution Data: Blockchain intelligence tools collect and analyze ownership attribution information for thousands of entities, which can be used to de-anonymize blockchain addresses for identification of criminals and investigative subjects. These systems rarely provide personally identifying information (PII) for individual owners of specific cryptocurrency assets, but may identify known associations with criminal groups or fraud schemes, as well as transactions with other relevant entities, such as exchanges and fiat off-ramps where criminal proceeds are converted to cash.
Transaction Mapping: Transactional data is converted into visual maps and flowcharts, showing interactions by the subject with known exchanges and other entities, tracing financial transfers to their ultimate endpoints. Visual mapping makes it much easier to recognize patterns, such as layering and peel chains, commonly used for money laundering. Expert investigators use powerful tools that automate mapping and evidence collection. This approach is more efficient and more effective than blockchain search engines or open-source explorers that require manual review of ledger entries.
Cluster Analysis: A cluster is a group of cryptocurrency addresses that are controlled by the same person or entity. Expanding the focus of an investigation from one address to a larger cluster can dramatically increase the amount of available evidence for de-anonymization and asset tracing. Cluster analysis can also be used to determine if any linked addresses have a substantial current value or UTXO.
Subpoena Targets: Commercial cryptocurrency exchanges, decentralized finance (DeFi) firms, and virtual asset service providers that comply with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations typically require verification of customer identity for new accounts. This makes them a highly valuable resource for de-anonymizing subjects who have used their services to buy, trade, hold, or cash-out cryptocurrency. Personally identifying information for registered owners of addresses and wallets – as well as their banking details – may be obtainable through civil subpoenas or criminal warrants.
Current/Historical Value: Cryptocurrency addresses with significant value are critical indicators for financial recovery. They may be appropriate targets for seizure warrants by criminal prosecutors, or garnishment during civil judgment enforcement.
Total Transactions: Volume of cryptocurrency transactions can signify the potential size of a fraud scheme and number of victims. Complaints to law enforcement typically receive more attention when a crime syndicate has harmed numerous people. Larger schemes may also be appropriate for class action suits in civil court.
Risk Profiling: Automated risk-scoring is conducted through advanced algorithms that trace activity of target address(es) and identify associations with known entities such as exchanges, mixers, peer-to-peer exchanges, sanctioned parties, ransomware rings, and darknet markets.
IP Address: Privacy-piercing metadata is collected through blockchain surveillance systems, which run networks of nodes that “listen” and “sniff” for Internet Protocol (IP) addresses associated with certain transactions. IP addresses, when available, may provide information regarding the geographical location of the subject at the time of the transaction.
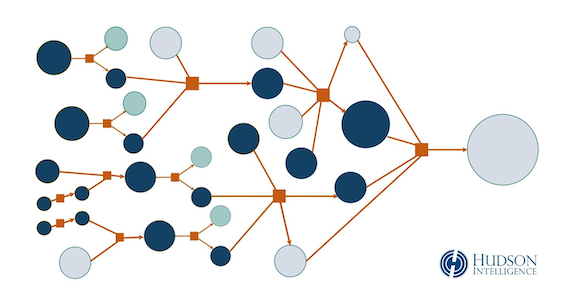
How to create a Finance business Risk Rule?
Combination of the risk rules as a business rules as below:
Rules as best example (Elliptic)
| Category | Description | Example |
|---|---|---|
| Activist Fundraising | Entities that have (a) either been convicted of a crime directly related to extremist activity or (b) have been identified and verified to have incited prejudice, violence and/or serious crimes. Elliptic maintains a rigorous and objective internal process when determining whether an entity should be ascribed to this label, based on the above conditions. | Pankkake (Anonymous Far Right Donor) |
| ATM | An automated teller machine at which cryptoassets can be sold and purchased for fiat currency; similar to a traditional bank-operated ATM. | ATM brands include SatoshiPoint, Lamassu, GenesisCoin |
| Authentication | A service that allows users to prove their unique identity without having to enter in their login credentials when accessing a particular website, thus increasing security. | Civic |
| Bitcoin Faucet | A type of website that at one time gave away Bitcoin for free. Now these websites usually reward users in the form of Bitcoin for completing tasks such as captchas. | Moonbit |
| Blockchain | Addresses linked to the operation of the blockchain. | TON Foundation |
| Bridge | A contract or service used to transfer assets from one blockchain to another. | Ren |
| Broker | An entity involved in the buying and selling of cryptoassets on behalf of clients. Unlike an exchange, a broker does not have an order book. |
Cumberland Mining |
| Charity | A non-profit or charitable organisation that accepts Bitcoin donations. | US Luge Foundation |
| Child Sexual Abuse Material Vendor | A vendor offering Child Sexual Abuse imagery for cryptoasset payment. | |
| Coin Swap Service | A crypto-to-crypto conversion service with fixed exchange rates that does often not require a user to login or any KYC. | ChangeNOW |
| Credit Card Data Vendor | An online carding shop, providing illicit credentials and other illicit personal financial information. | JokerStash.store |
| Criminal Organisation | A group of multiple individuals involved in organised crime. | The Shadow Brokers |
| Crypto-Exchange | An exchange where customers can only trade cryptoassets in exchange for other cryptoassets. | Poloniex |
| Dark Forum | A TOR-only accessible online discussion forum | DNM Avengers |
| Dark Market - Centralised | A TOR-only accessible marketplace selling illegal goods and services with a centralised infrastructure. The marketplace has its own wallet infrastructure and holds users keys on it. Individuals making and receiving purchases interact with the marketplace, rather than with the seller or buyer directly. |
Dream Market |
| Dark Market - Decentralised |
A TOR-only accessible marketplace selling illegal goods and services with a decentralised infrastructure. The marketplace does not have its own wallet infrastructure. Individuals making and receiving purchases interact directly with the seller or buyer. |
Wall Street Market |
| Dark Service | An illicit service, including hacking, wallet, and web hosting services. | PinPays |
| Dark Vendor Shop | A TOR-only accessible individual vendor shop on a dark marketplace that sells illegal goods and services. | Euroarms |
| Data | A vendor that provides data for the end user, such as details regarding the bitcoin address owner, such as username and email address. | BitcoinWhosWho |
| De-Fi | A decentralised financial platform, usually run through a smart contract. | MakerDAO |
| Decentralised Exchange | A decentralised service that provides crypto-to-crypto exchange services, such as Bitcoin to Ethereum. | Uniswap |
| Entertainment | A vendor that provides streaming, TV, films, and other entertainment services. | |
| Escrow | A vendor that provides escrow services for a transaction between two parties. | Safe Lock |
| Exchange | A centralised service that provides fiat-to-crypto exchange services, such as USD to bitcoin. The exchange may also provide crypto-to-crypto exchanges services, such as Bitcoin to Ethereum. |
Coinbase |
| Extortion | The use of force or threats to obtain funds from an individual or multiple individuals. | Ashley Madison Extortion |
| Financial Services | A financial services organisation providing financial services, such as loans, bonds, and derivatives products. | Bitbond |
| FinCEN Primary Money Laundering Concern | FinCEN uses this designation when it has identified a financial institution, jurisdiction, or type of account as being of significant risk for money laundering or the financing of terrorism. | Bitzlato - FINCEN Section 9714 - January 18 2023 |
| Forum | An online discussion forum. | |
| Gambling | Gambling services. | BetChain |
| Hardware Wallet | A physical hardware wallet to store cryptoassets; located often on a separate external hard drive with the purpose of providing additional wallet security. | Bitcoin Paper Wallet |
| High Transaction Fee | A transaction involving a higher than average transaction fee to miners, suggesting possible loss or criminal activity. | High Transaction Fee Sender (Block 7238273) |
| Hosting | Website hosting service. | Torservers.net |
| Investment Syndicate | A group investment provider, such as a cryptoasset venture operator or multi-level marketing scheme. | Coinsilium |
| Known Criminal | A Known Criminal is a known individual involved in illicit activity. A Known Criminal is often linked to a Criminal Organisation. | Ross Ulbricht and Carl Mark Force |
| Law Enforcement | A known law enforcement entity. | FBI |
| Layer 2 | A blockchain scaling solution built on a “Layer 1” blockchain, typically enabling faster transactions with lower fees, while retaining the security of the Layer 1 protocol. | Lightning Network |
| Malware | Software that is intended to damage or disable computers and computer systems. | Trickbot |
| Marijuana Vendor Shop | A marijuana dispensary, registered in a regulated jurisdiction. | Speedweed |
| Merchant | Online licit merchants or vendors. | Mypayingcryptoads |
| Microtransactions Service | Website promoting microtransactions, for example freelance work, web plugins generating cryptoassets. | coinworker |
| Mine | Newly minted cryptoassets which are created as part of the mining/validating process. | The bitcoin which is paid to miners as the block reward and transaction fees |
| Miner | A service that mines and generates new cryptoassets. | BTC.TOP |
| Misc Service | A miscellaneous uncategorized service, vendor, or organisation. | Coinfirm |
| Mixer | A service that allows for cryptoassets mixing or tumbling in order to anonymise funds. Used for both privacy purposes and also for laundering funds. | Chip Mixer |
| News | An online news publishing service. | ProPublica |
| NFT Marketplace | A marketplace enabling creators to sell NFTs to its users. | OpenSea |
| OFAC Sanctioned Entity | An entity sanctioned by the Office of Foreign Assets Control (OFAC) of the US Department of the Treasury. | Garantex Europe OU - OFAC SDN - 5 Apr 2022 |
| Outsourcing Provider | A website promoting freelance opportunities. | coinworker |
| Payment Services Provider | A service offering the ability to accept online payments through a variety of payment methods, including cryptoassets. | BitPay |
| Peer to Peer Exchange | A platform on which individual buyers and sellers can exchange cryptocurrency for other payment types with one another. | |
| Phishing | A form of fraud in which a message sender attempts to trick the recipient into divulging important personal information like a password or bank account number, transferring money or installing malicious software. Usually, the sender pretends to be a representative of a legitimate organisation. | TRON Web Wallet Phishing (https://tron-block.com) |
| Political Campaign | A political campaign or organisation. | Alexey Navalny Campaign |
| Ponzi Scheme | A form of fraud in which belief in the success of a nonexistent enterprise is fostered by the payment of quick returns to the first investors from money invested by later investors. | Jetcoin |
| Privacy Wallet | A crypto wallet that offers features helping users to avoid de-anonymization on the blockchain. This could be by allowing them to participate in coinjoin transactions, or by providing a built-in mixer service, among others. |
Wasabi wallet |
| Ransomware | A type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. | WannaCry 2.0 |
| Reported Loss | Purported loss of cryptoasset often due to destruction or a fork. Unlike a theft, the funds associated with a loss are no longer accessible, as a loss often involves the destruction of private keys. | October 2011 Mt. Gox Loss |
| Research Chemicals | Bulk chemical retailers for laboratory use only. However, in practice, research chemicals are often used to produce illicit drugs. |
Buckled.eu |
| Scam | Any other type of fraudulent scheme. | Prodeum |
| Shielded | A shielded address uses cryptographic techniques to obscure on-chain information such as addresses and amounts | |
| Software Development | A software development organisation. | GIMP |
| Software Wallet | An intangible software wallet to store cryptoassets, located on an online platform, individual’s computer, or external hard drive. | MyBitcoin |
| Terrorist Organisation | An organisation involved in terrorism or related activity. | ISIS |
| Thief | Recipient of stolen funds. | Stolen CoinSecure Funds |
| Token | Tokens are a representation of a particular asset or utility, that resides on top of another blockchain, such as Ethereum. Tokens can represent a range of fungible assets, such as property, to assets that are intangible, like Cryptokitties, and cryptoassets, like EOS. |
EOS |
| Token Sale | A Crowdsale, pre-sale, or otherwise sale associated with the launch of a Token or other cryptoasset. | Atlant Token Crowdsale |
| Trading Platform | An exchange software and services provider. This entity does not operate exchanges but provides the software to operate them. |
Alphapoint |
| User | A forum or social media user. | Niktitan132 |
| Unknown | An “unknown” entity or category means the address is not labeled in the Elliptic system. This means we do not recognize the address as being controlled by any specific entity. | |
| Validator | A Validator for a Ledger-based currency. | |
| Venture Capital | A venture capital organisation working with startups, early-stage, and emerging companies that have been deemed to have high growth potential. | Alter VC |
| VPN Vendor | A vendor that provides Virtual Private Networks (VPN) services. | SecureVPN |
Entity Naming Conventions as best example
| Entity Name | Description | Category |
|---|---|---|
| Fraud Incident & Customer Submitted Fraud Incident | These are client-submitted incidents involving fraudulent activity, such as the use of fraudulent credit card data. It is placed within the Thief category but the identity of the actor is unknown eg. Fraud Incident - 1171161288 | Thief |
| Blacklisted Address | A token issuer has blacklisted these addresses. Elliptic does not have any information regarding why the address is blacklisted. Contact the issuer for more details, eg. USDT Blacklisted Address - 57492936 | Scam |